- June 2, 2023
- Posted by: Admin
- Category: Cybersecurity

Top Cloud security threats in 2023 and How to tackle them
Cloud adoption has dramatically improved business productivity and efficiency regardless of the industry they belong to. Businesses of all sizes depend heavily on cloud computing these days. However, the migration to the cloud has many security flaws that need continuous monitoring and analysis.
Every organization needs a solid strategy to ensure smooth business flow and stay out of these cloud threats. Due to the spike in cloud security threats in the past decades, cloud security solutions have become a critical tool for organizations. Decision makers have to understand the most critical Cloud security issues and implement the best possible solutions to build a robust cloud security strategy.
This article will discuss top Cloud security threats in 2023 and how businesses can stay away from all kinds of potential threats.
Top Cloud Security Threats in 2023 and Solutions
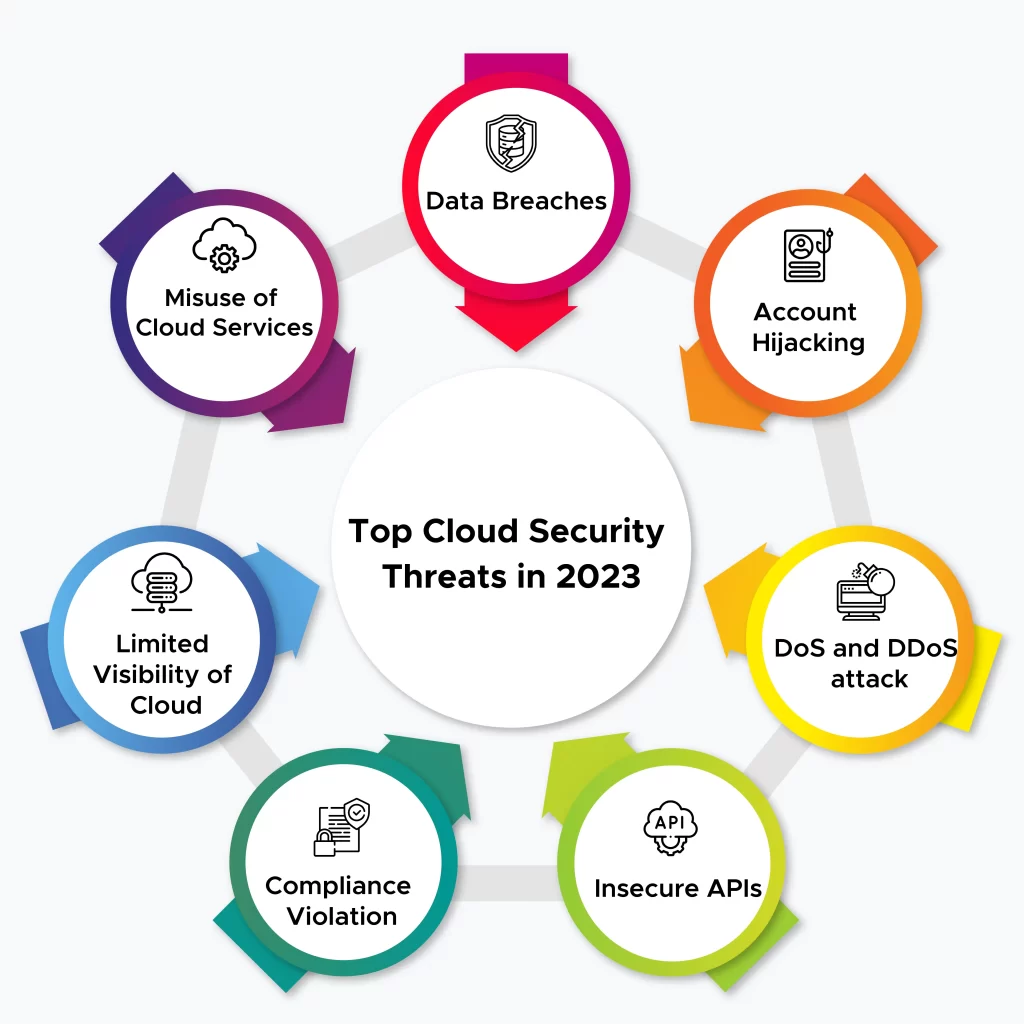
Cloud computing has redefined the way businesses use and transfer data is constantly evolving. Sensitive data is potentially at risk as cloud computing usage grows globally. Let’s look at the main Cloud security issues and threats in 2023 and how to overcome those risks and safeguard any organizations:
Data breaches
A data breach occurs when unauthorized people get access to organizational data, such as sensitive business data, personal data, or financial data. Data breaches could harm a business’s reputation, and result in loss of customer trust. The frequency of data breaches is increasing and businesses must take precautions to protect their sensitive data. This refers to having strong security measures in place, frequent system checkups, and educating employees to follow the best security practices.
Solution
Multi-level security measures have to be implemented other than username and password. For example, setting up multi-factor authentication or a one-time password can help prevent unauthorized access that causes data breaches. Encrypting organizational data is another way to prevent potential data breaches. Organizations can protect sensitive data before it gets migrated to the cloud by encrypting it. No one can decrypt it without having the decryption details. Presently, these are the best proactive measures to handle data breach issues.
Account hijacking
It refers to unauthorized access to cloud accounts followed by stolen or lost login credentials. Due to this type of attack, organizations may face data theft, financial loss, and reputational impact. Scammers hijack an individual’s account by getting their login credentials through malware attacks, phishing scams, or data breaches. They use this information to get into the victim’s Cloud account thereby accessing sensitive data, including financial or identity-related information.
Solution
The best solution is to establish a transparent access management system throughout the organization. Access management determines the accessibility of the data for different users. This will prevent the overlapping of data between various departments and help protect confidential information.
DoS and DDoS attack
DoS, also known as Denial of Service attack is becoming more common these days. Despite not being the same as hacking, a DoS attack cuts access to the system. The purpose of a DoS attack is to prevent users from using the programs or creating hindrances to their activities. Whereas, DDoS attacks are a type of attack in which the hacker send huge traffic to the victim’s site or application. This way, the system will be unable to handle the load and eventually stops working or crash.
Solution
Firewalls can be set to monitor the traffic and its source. This helps to identify and eliminate fake traffic that’s been sent by the attacker. Another way to avoid this type of attack is to block the IP addresses that might lead to an attack. Businesses can also try using tools like Intrusion Detection Systems (IDS) to protect against DoS attacks. IDS detects and identifies fake traffics by constantly monitoring it.
Insecure APIs
Application Program Interfaces (API) enable a program to communicate across various systems and applications. APIs play an important role in the cloud architecture. Attackers can make use of APIs to hack organizational details, thereby collecting sensitive data and information. The reason an API is prone to attack is many. A few of them are poor design structure, lack of proper implementation, not so well defined processes, procedures and authorization, etc. Attackers can leverage these loopholes to access sensitive data.
Solution
Penetration testing allows organizations to assess their system’s security and identify improvement areas. This testing is performed by simulating an external attack on API endpoints, thereby trying to break the security and get access to the company’s private data. Testers use various testing practices to detect API vulnerabilities so that organizations can focus on fixing the same.
Compliance violation
Over the past decades, companies heavily rely on cloud-based ecosystems to boost accessibility and scalability. However, it comes with various compliance issues. Any violation of these compliances- accidentally or purposefully can cause potential risks to organizations. It could be in the form of paying fines to regulatory bodies and all.
Solution
Setting up well-defined privacy and compliance frameworks to protect organizational resources to stay away from compliance violations is the best practice. A governance framework should also be in place for monitoring organizational duties and responsibilities. Also, defining the duties and roles assigned to each employee is essential to specify how they interact with one another.
Limited visibility of Cloud
In some cases, the visibility and access to the data are lost when migrating to the cloud. In such cases, it can lead to data breaches and loss because it exposes risks associated with bad governance and insufficient security.
Solution
To stay out of this threat, it is advised to perform risk assessments test on a regular basis. Also, make sure that the cloud service provider has regular audits and security measures to protect user data. Hiring the best cloud security company is also highly suggested.
Misuse of Cloud services
When someone inside an organization uses the organizational cloud services for personal or other illicit activities, its termed as cloud service misuse. The improper usage of Cloud services might put sensitive data at risk and may even affect confidential
Solution
Developing and implementing clear policies and standards for using cloud resources is the first step to preventing the misuse of cloud services. Educating employees and providing proper training on these policies can also be done to prevent the misuse of Cloud services. Thorough monitoring and check-up of cloud usage resources and access logs are highly recommended.
Conclusion
With the evolution of technology, we may also face various types of attacks on sensitive data. Techniques practiced by attackers to implement these data attacks will also evolve. As the world of cloud security is constantly changing, it’s critical for decision-makers and organizations to stay updated with the latest threats and best practices to get rid of these threats. By practicing and implementing the above-mentioned practices, organizations can reduce their chances of facing potential security risks in 2023. Hire a reliable and trustworthy cloud solution service provider and cloud security company in Bangalore like DxMinds to eliminate any Cloud security challenges and risks. For more details, drop a mail to info@dxminds.com